Want to pass OSCP from scratch? This step-by-step guide covers everything—from basics to labs—to help you master ethical hacking and ace the OSCP exam!
What is OSCP?
OSCP is a penetration testing certification offered by Offensive Security. It requires candidates to complete a 24-hour hands-on exam, where they must compromise multiple machines and submit a detailed report. The exam tests your ability to think critically, apply hacking methodologies, and work under pressure.

Prerequisites for OSCP
While there are no official prerequisites, having some background knowledge can be beneficial. You should have:
- Basic knowledge of Linux and Windows operating systems
- Familiarity with networking concepts (TCP/IP, ports, protocols)
- Basic programming/scripting skills (Python, Bash)
- Understanding of fundamental cybersecurity concepts
If you’re starting from scratch, don’t worry! Follow this structured roadmap to prepare for OSCP effectively.
Step 1: Build a Strong Foundation
Before diving into penetration testing, you need a solid understanding of basic cybersecurity and networking concepts.
Learn Networking and Linux Basics
- Networking: Study TCP/IP, subnetting, DNS, and VPNs.
- Recommended resources:
- “Networking Basics” by Cisco
- “CompTIA Network+” certification materials
- Recommended resources:
- Linux Fundamentals: Learn common Linux commands, file permissions, and scripting.
- Recommended resources:
- “The Linux Command Line” by William Shotts
- OverTheWire: Bandit (Linux challenges)
- Recommended resources:
Learn Programming for Pentesting
While programming isn’t mandatory, it helps in automation and exploit development. Focus on:
- Python for scripting and automation
- Bash for command-line efficiency
- Basic C and Assembly for exploit development
- Recommended resources:
- “Automate the Boring Stuff with Python”
- “Hacking: The Art of Exploitation” by Jon Erickson
- Recommended resources:
Step 2: Learn Ethical Hacking Fundamentals
Now that you have the basics down, start learning ethical hacking methodologies.
Familiarize Yourself with Ethical Hacking Concepts
Learn about:
- Footprinting and reconnaissance
- Scanning and enumeration
- Exploitation techniques
- Privilege escalation
- Post-exploitation
Hands-on Labs and Practice
- TryHackMe (Beginner-friendly cybersecurity training)
- Hack The Box (Intermediate to advanced labs)
- PentesterLab (Web and application security)
Start solving easy machines and gradually move to more complex ones.

Step 3: Master Penetration Testing Methodology
Now, it’s time to focus on penetration testing techniques and tools.
Familiarize Yourself with Pentesting Tools
Some essential tools you need to master:
- Nmap – Network scanning
- Burp Suite – Web application testing
- Metasploit – Exploitation framework
- John the Ripper – Password cracking
- Wireshark – Network analysis
- Gobuster/Dirb – Directory brute-forcing
- Netcat – Networking and shell interactions
Practice using these tools in real-world scenarios.
Follow the OSCP-Like Approach
- Enumerate thoroughly before attempting an exploit.
- Try manual exploitation before using automated tools.
- Document every step to help with your exam report.
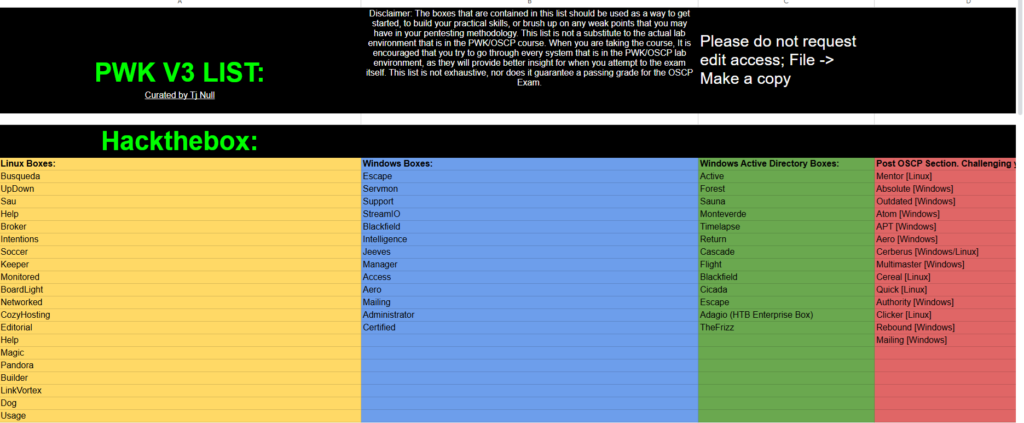
Also at the same time, I solved the HTB Boxes from TJNull List
https://docs.google.com/spreadsheets/u/1/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/htmlview
Above is a list of those boxes, sorted based on severity & target OS (Windows or Linux).
Now start learning; aim to solve at least 1–2 boxes per day. For example, if you are learning Windows Privesc, side by side, get hands-on by solving Windows Boxes. Also made a write-up kind of notes for all the boxes I have solved for your personal reference and got the skill of solving & documenting at the same time. This is also VERY important, as in the future, if you encounter the same service in any other box, you can easily search through it and use the same commands and steps.
Focused on easy boxes of TJNull and once got comfortable, went to medium boxes and then hard boxes.
Step 4: Enroll in PWK and Start OSCP Labs
The Penetration Testing with Kali Linux (PWK) course is the official training for OSCP. When you enroll, you get access to:
- OSCP course materials
- 60+ hands-on penetration testing labs
- OSCP exam registration
How to Approach OSCP Labs?
- Start with easy machines and progress to harder ones.
- Follow a structured approach: Enumeration → Exploitation → Privilege Escalation.
- Take notes and document every step.
- Aim to complete at least 40-50 lab machines before taking the exam.
Step 5: Prepare for the OSCP Exam
The OSCP exam is a 24-hour challenge where you must:
- Hack into multiple machines
- Gain administrator/root privileges
- Submit a detailed report with proof of exploitation
Exam Tips:
- Manage your time wisely (start with the easier machines first)
- Enumerate thoroughly before jumping to exploits
- Take breaks to avoid burnout
- Keep a well-structured notes repository
Report Writing:
- Document every step, including commands used and screenshots
- Follow Offensive Security’s exam report template
- Make your report clear, concise, and professional
Final Thoughts
Preparing for OSCP from scratch may seem overwhelming, but with the right approach, anyone can do it. Build a strong foundation, practice consistently, and approach the exam with confidence. Remember, OSCP is not just about passing an exam—it’s about developing real-world penetration testing skills.
Bonus Resources
Good luck with your OSCP journey! Stay persistent and never stop learning.

Read More Blogs Here!

Passing the OSCP from scratch sounds like a challenging yet rewarding journey. I appreciate the structured roadmap provided in this guide—it makes the process feel more approachable. The emphasis on building a strong foundation in cybersecurity and networking is crucial, and I agree that hands-on practice is key. The 24-hour exam seems intense, but it’s great that it mirrors real-world scenarios. I wonder, though, how much time one should realistically dedicate to preparation before attempting the exam? Also, do you think focusing on specific tools or methodologies gives an edge, or is it better to have a broad skill set? Overall, this guide is motivating, and I’m curious to hear from others who’ve taken this path—what was your experience like?
As for tools, mastering Privilege Escalation techniques, Buffer Overflow, and tools like Burp Suite, LinPEAS, and BloodHound can be tricky at first but essential. Focus on understanding the process, not just the tools. A broad skill set helps, but strong fundamentals and methodology matter most. Stick with it—you’ll get there!
The OSCP journey seems intense but incredibly rewarding! I’m curious, how much time did it take you to feel confident enough to attempt the exam? The 24-hour hands-on challenge sounds both exciting and nerve-wracking. I wonder if there’s a specific tool or technique that you found most challenging to master? Also, do you think someone with minimal programming knowledge can still succeed, or is it a must-have skill? The structured roadmap is helpful, but I’d love to hear more about your personal experience—what was the biggest hurdle you faced? And finally, do you have any tips for staying motivated during the preparation phase?
The OSCP journey is definitely intense but worth it. For most beginners, it takes around 4–6 months of consistent study (15–20 hours/week) to feel confident. The 24-hour exam is tough but manageable with regular practice and mock simulations.
You don’t need to be a programming expert—basic Python, Bash, and scripting knowledge is enough. Many succeed with minimal coding experience by focusing on enumeration, exploitation, and methodology. The most challenging part for many (including me) is staying motivated and not burning out. Breaking the journey into milestones, joining online communities, and tracking small wins helps a lot.
OSCP sounds like a challenging but rewarding certification to pursue. I appreciate the step-by-step approach outlined here, especially for beginners like me. It’s great to see a roadmap that starts with the basics and gradually builds up to more complex challenges. The emphasis on consistent practice and real-world skills is motivating. Do you think it’s possible to pass OSCP without any prior experience in cybersecurity? I’m curious about how much time one should ideally dedicate to preparation before attempting the exam. Good luck to everyone starting this journey—let’s keep learning and pushing our limits!
Absolutely! Yes, it’s possible to pass the OSCP without prior cybersecurity experience if you’re consistent and dedicated. Start with basics like networking, Linux, and simple scripting (Python/Bash), then move on to hands-on labs. Ideally, you should prepare for 4–6 months with 15–20 hours per week of focused practice. Stick to a structured plan, take good notes, and practice like it’s the real exam. You’ve got this—keep pushing forward!
This guide is incredibly detailed and seems like a solid roadmap for anyone aiming to tackle the OSCP certification. I appreciate how it breaks down the process from scratch, making it accessible even for beginners. The emphasis on understanding basic cybersecurity concepts before diving into penetration testing is crucial, and I think it’s a smart approach. The suggestion to focus on tools and real-world scenarios is spot on, as hands-on experience is essential in this field. However, I’m curious—how much time would you realistically recommend someone spend on each phase of this roadmap? Lastly, do you think someone with minimal IT experience but a lot of determination could realistically pass OSCP following this guide? What’s your take on that?
There is no time limit. It varies from person to person. Once you feel confident about the concept, then move to the next, and if you feel that you are losing at some point, get back to it and learn. For basics, one month is enough. As i already mentioned, experience helps but is not required. you just need a few concepts:
Networking (TCP/IP, ports, protocols)
Linux and Windows basics
How web applications work
Common attack vectors (e.g., SQLi, XSS, LFI/RFI)
Starting your OSCP journey from scratch is definitely challenging but seems manageable with the right roadmap. I love how detailed the guide is, breaking things down from basics to advanced labs. The emphasis on hands-on practice makes a lot of sense, especially for something as practical as penetration testing. Do you think someone with zero programming experience can still succeed in the exam if they focus on other areas? Also, how important is it to have prior experience with cybersecurity before starting OSCP? The idea of the 24-hour exam sounds intense, but I guess consistent practice would help build the needed stamina. Overall, this guide seems like a solid plan—would you recommend any additional resources or tips for someone just starting out? Let’s discuss!
First of all, Programming is helpful, not mandatory. The exam doesn’t test deep coding skills, but basic scripting (especially in Python, Bash, and PowerShell) is extremely useful for writing custom exploits and understanding how things work under the hood. The concepts of networking and linux are mandatory. Secondly, experience helps but is not required. you just need a few concepts:
Networking (TCP/IP, ports, protocols)
Linux and Windows basics
How web applications work
Common attack vectors (e.g., SQLi, XSS, LFI/RFI)
At last, key to handle 24 hour exam is just practice, practice and practice
Practicing 3-4 hour lab sessions regularly
Simulating the exam environment before the real test (e.g., using VulnHub or HTB Pro Labs for 8-12 hour sessions)
Maintaining notes in tools like CherryTree, Obsidian, or OneNote.
Thank you, I value this!
casino en ligne
Nicely put. Cheers!
casino en ligne
Regards. A lot of information.
casino en ligne
Thank you! I enjoy this.
casino en ligne fiable
You suggested it exceptionally well!
casino en ligne France
Beneficial data Cheers.
casino en ligne fiable
Thanks a lot. Good information!
casino en ligne fiable
Helpful forum posts Thanks a lot!
casino en ligne
Whoa all kinds of beneficial material!
casino en ligne
You said it adequately..
meilleur casino en ligne